I wrote about digitally signing programs for Windows a few years ago. Microsoft announced last year that windows would no longer trust files signed with the SHA-1 algorithm after 1 January 2017. This causes some problems with older operating systems (like XP SP2 and Vista) as they do not support the SHA256 algorithm for certificates used to sign programs/apps. To maintain compatibility with ealier versions Microsoft suggests dual signing with both the SHA1 and SHA256 certificates. It turns out my certificate (from Comodo and issued in mid-2015) supports both the SHA1 and SHA256 algorithm so it’s not a big hassle for me. However, some older certificates (that have not expired) may need to be re-issued by the issuing authority, some certificate issuers such as K-Software are issuing replacements for free.
Here’s what I had to do to sign my EXE files with both SHA1 and SHA256 versions of my certificate.
1. Download an up-to-date version of the signtool.exe file from Microsoft. Such as this one from the Windows 8.1 SDK.
2. My certificate was installed automatically by Comodo when I purchased it so it needed to be exported to a PFX file. You’ll need to know what the password for your certificate was when you purchased it. There’s a decent tutorial covering this process here.
3. Work out the new commands to dual sign your EXE files. In my case they look something like this.
//Code sign with SHA1 signtool.exe sign /f "c:\path\to\pfx-file\my-pfx-file.pfx" /p mypfxpassword /t http://timestamp.comodoca.com /v c:\Path\To\File\somefile.exe //Code sign with SHA256 signtool.exe sign /f "c:\path\to\pfx-file\my-pfx-file.pfx" /p mypfxpassword /fd sha256 /tr http://timestamp.comodoca.com/?td=sha256 /td sha256 /as /v c:\Path\To\File\somefile.exe
It’s important to use the /fd and /td switches on the second call to ensure both the file and date/time stamp are SHA256 signed. I actually wrote a little batch file to automate the dual signing of files. I call the file from my various build scripts to sign both my program executables and installers. Here’s that file:
@echo off echo ************************************************ echo Running %0 IF %1=="" GOTO InvalidParameter IF not exist %1 goto InvalidFile echo Signing %1 echo Signing with sha1 "d:\code signing 256\signtool.exe" sign /f "c:\path\to\pfx-file\my-pfx-file.pfx" /p mypfxpassword /t http://timestamp.comodoca.com /v %1 echo Signing with sha256 "d:\code signing 256\signtool.exe" sign /f "c:\path\to\pfx-file\my-pfx-file.pfx" /p mypfxpassword /fd sha256 /tr http://timestamp.comodoca.com/?td=sha256 /td sha256 /as /v %1 echo Signing completed Successfully goto eof :InvalidParameter echo You must pass this script a file to sign goto eof :InvalidFile echo %1 does not exist goto eof :eof echo ************************************************
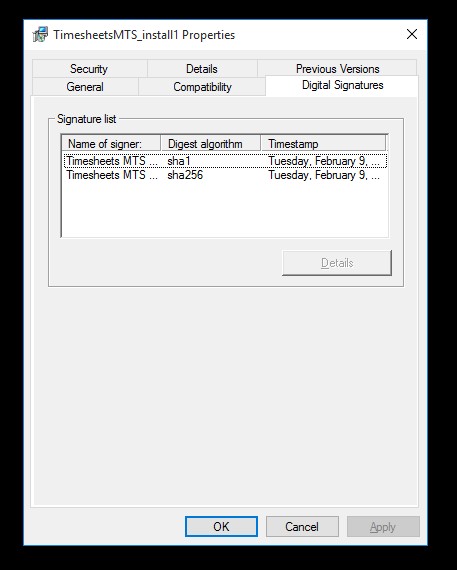
You can easily check if you’ve dual signed correctly from within Windows 10 by right clicking on your signed EXE file, selecting Properties and then clicking the Digital Signatures tab. If it’s done right it should look something like the screen below. Note that both the SHA1 and SHA256 certificates are present.